Crackme 0x02
I’ve recently started doing the Modern Binary Exploitation challenges, and figured i’d do writeups on them to consolidate my learning as I went.
Start
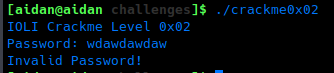
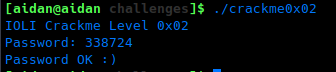
Marking crackme0x02 as executable with chmod +x crackme0x02 and running it provides with with a prompt to enter a password:
Ghidra
Opening this up in Ghidra, we can open up the function list on the left menu 
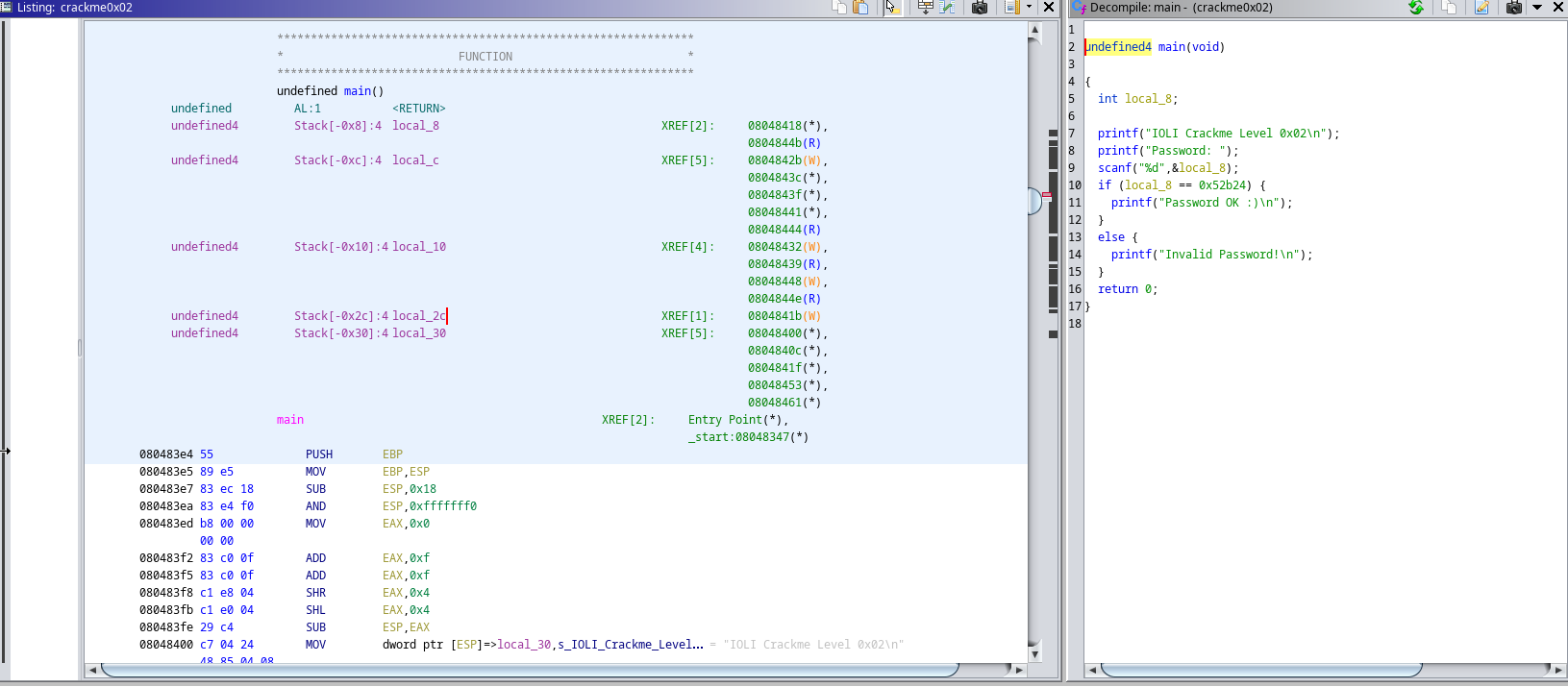
And we can see that it contains the main function if we scroll down:
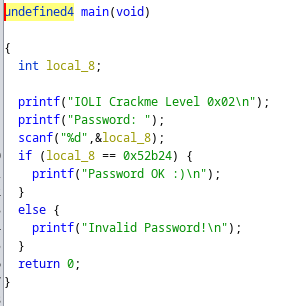
This program has not been stripped of it’s debug symbols, so we can still see function names thankfully. Inside of the main function we have this:
Taking a look at our decompiled main, it looks like if the password we enter is equal to 0x52b24 we have found the correct password.
This is a hexadecimal number, so lets convert it to binary and give it a try!
Great, so this works but how does the assembly code work? I decided to try tracing the assembly code and this is what I came up with:
Below is the original ASM code, then my interpretation of the code
1
2
3
4
5
6
7
8
9
10
MOV dword ptr [EBP + local_c], 0x5a00
MOV dword ptr [EBP + local_10], 0x1ec00
MOV EDX, dword ptr [EBP + local_10]
LEA EAX+local_c, [EBP + -0x8]
ADD dword ptr [EAX]+local_c, EDX
MOV EAX+local_c, dword ptr [EBP + -0x8]
IMUL EAX, dword ptr [EBP + local_c]
MOV dword ptr [EBP + local_10], EAX
MOV EAX, dword ptr [EBP + local_8]
CMP EAX, dword ptr [EBP + local_10]
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
mov [EBP + local_c], 0x5a
local_c = 0x5a
local_c = 90
mov [EBP + local_10], 0x1ec
local_10 = 0x1ec
local_10 = 492
mov EDX, [EBP + local_10]
EDX = local_10
EDX = 492
lea EAX+local_c, [EBP + -0x8]
EAX = *local_c
EAX = 90
add [EAX]+local_c, EDX
local_c = local_c + EDX
local_c = 90 + 492
local_c = 582
mov EAX+local_c, [EBP + -0x8]
EAX = local_c
EAX = 582
imul EAX, [EBP + local_c]
EAX = EAX * (EBP + local_c)
EAX = 582 * 582
mov dword ptr [EBP + local_10],EAX
local_10 = EAX
local_10 = 338724
mov EAX,dword ptr [EBP + local_8]
EAX = local_8
cmp EAX,dword ptr [EBP + local_10]
EAX == local_10
input == 338724
Conclusion
After doing both static analysis with Ghidra and a stack trace of the assembly code, we can see that the password 338724 works, and we have successfully cracked this program!